In the ever-evolving landscape of cloud computing, the adoption of AWS (Amazon Web Services) data lakes has become a strategic imperative for organizations seeking to harness the power of big data. These data lakes serve as centralized repositories, allowing businesses to store, manage, and analyze vast amounts of structured and unstructured data from a variety of sources. However, Nettruyen with the increasing aws security data lake volume and complexity of data, the need for robust security measures has become paramount.
Securing Your AWS Security Data Lake: Best Practices for Data Protection
The AWS data lake, with its robust features and scalability, presents a compelling solution for organizations looking to unlock the value of their data. Yet, the very nature of aws security data lake this platform also introduces unique security challenges that must be addressed to ensure the confidentiality, integrity, and availability of sensitive information.
One of the primary concerns in securing an aws security data lake is protecting the data itself. The data stored within the lake can encompass a wide range of sensitive information, including customer records, financial transactions, and proprietary intellectual property. Unauthorized access or data breaches can have severe consequences, ranging from financial losses and reputational damage to regulatory non-compliance and legal liabilities.
To mitigate these risks, organizations must implement a comprehensive security strategy that encompasses multiple layers of protection. This begins with the foundational step of aws security data lake properly configuring the AWS data lake infrastructure, which includes setting up appropriate access controls, encryption, and logging mechanisms.
Access control is a critical component of aws security data lake. By leveraging AWS Identity and Access Management (IAM), organizations can establish granular permissions, ensuring that only authorized users and applications have access to specific data sets or resources within the data lake. This level of control helps prevent unauthorized access and minimizes the risk of data breaches.

Encryption is another essential safeguard for aws security data lake the data within the AWS data lake. By employing server-side encryption with AWS-managed keys or customer-managed keys, organizations can ensure that the data is protected at rest. Additionally, the use of client-side encryption can provide an extra layer of security by encrypting the data before it is uploaded to the data lake.
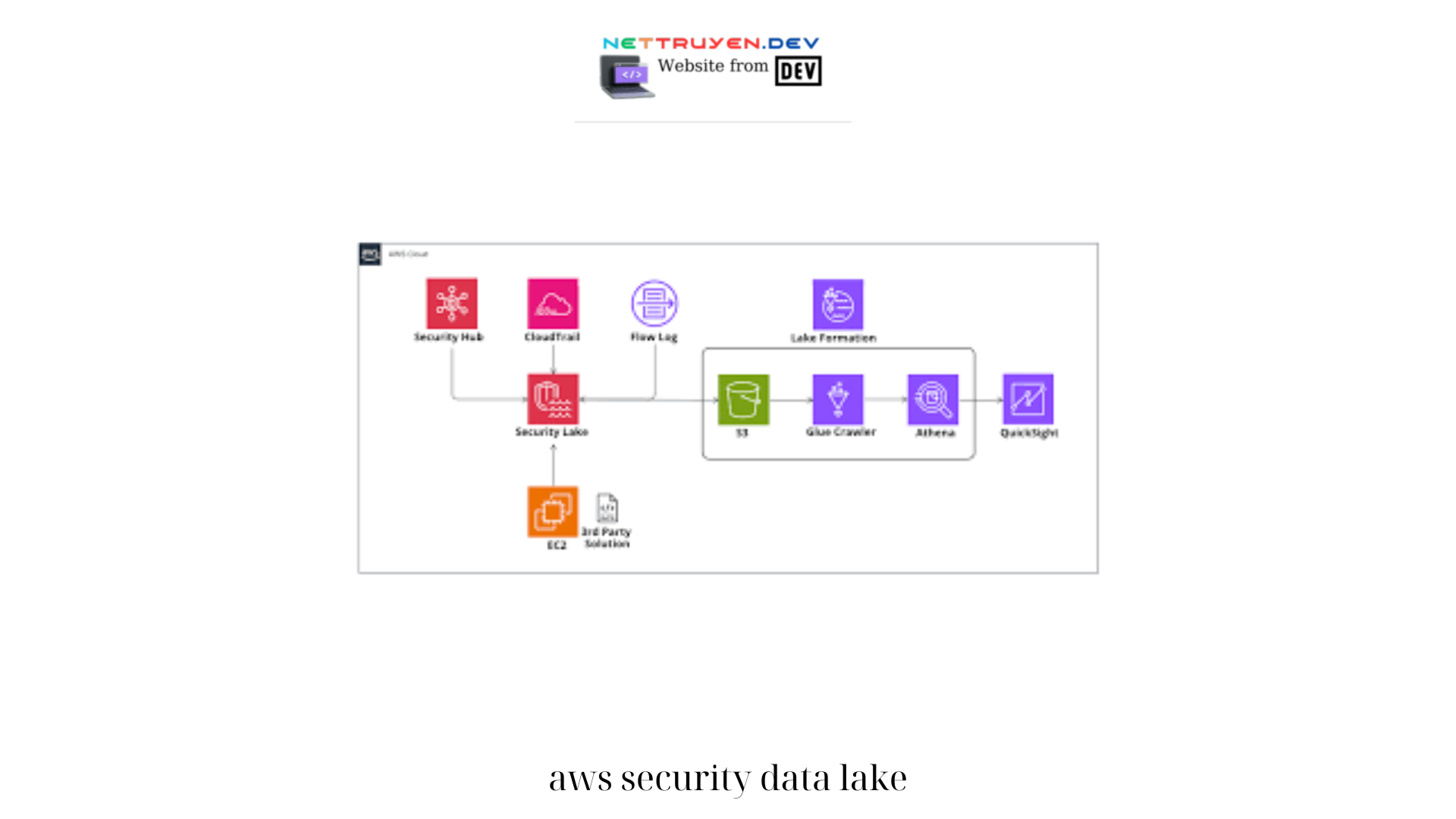
Another important consideration in securing an AWS data lake is the integration of other AWS services. By leveraging complementary services, such as AWS Glue for data transformation, AWS Athena for querying, and Amazon Elasticsearch Service for analytics, organizations can create a robust and aws security data lake cohesive security ecosystem. This level of integration ensures that security controls are consistently applied across the entire data management landscape.
It is also crucial for organizations to establish and regularly review their data governance policies. These policies should define clear guidelines for data classification, access privileges, and aws security data lake incident response procedures. By aligning these policies with industry standards and regulatory requirements, organizations can ensure that their AWS data lake remains compliant and secure.
Logging and monitoring are also crucial elements of a robust security strategy. AWS provides comprehensive logging capabilities, such as AWS CloudTrail and Amazon CloudWatch, which enable organizations to track and analyze user activities, API calls, and other events within the data lake. This aws security data lake information can be invaluable for detecting and responding to potential security incidents, as well as for compliance and auditing purposes.
Beyond the technical aspects of securing the data lake infrastructure, organizations must also address the human factor in data security. Comprehensive security awareness training for employees, including best practices for data handling, password management, and incident response, can help mitigate the risk of insider threats and social engineering attacks.
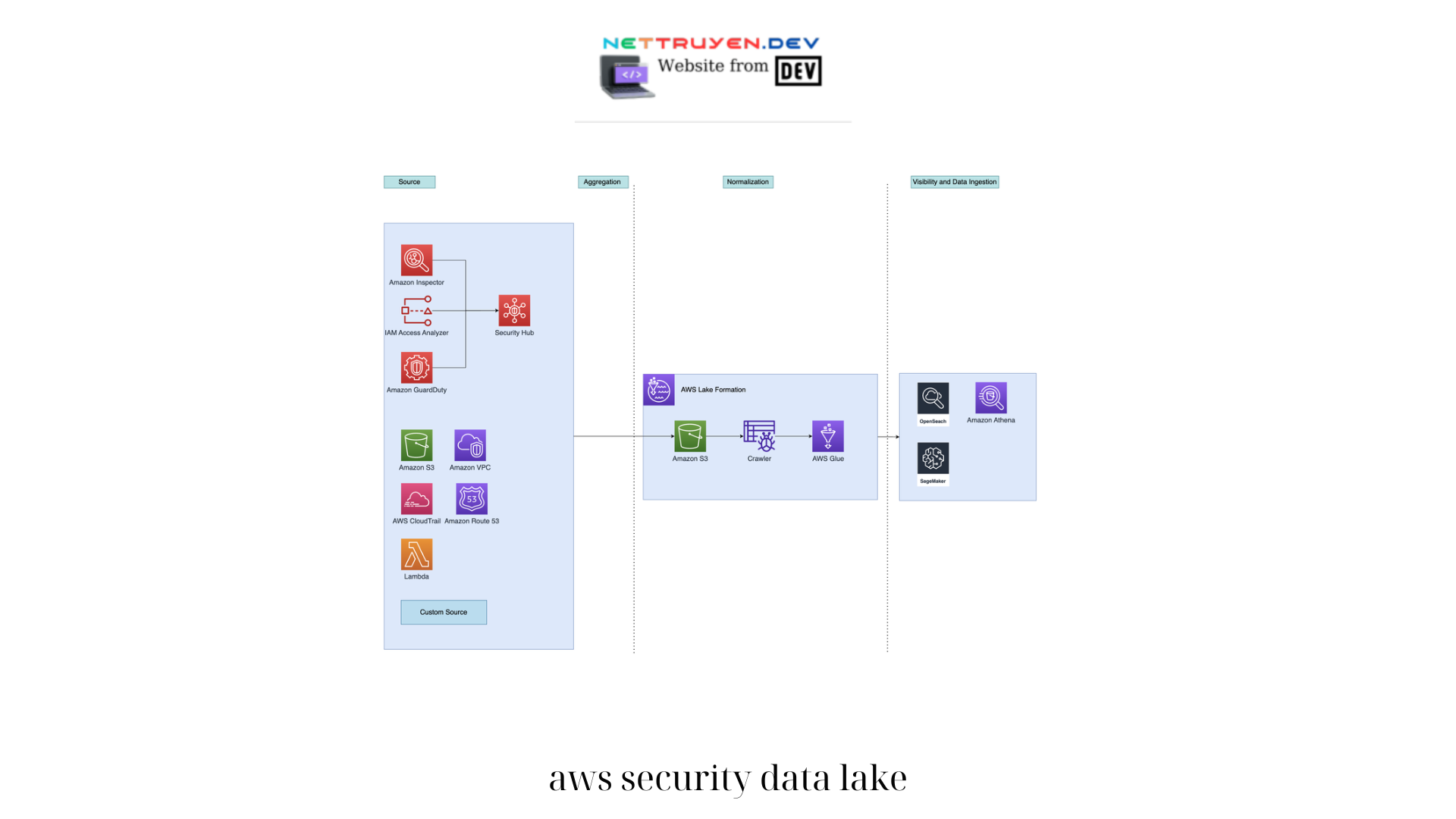
Another important consideration in securing an AWS data lake is the integration of other AWS services. By leveraging complementary services, such as AWS Glue for data transformation, AWS Athena for querying, and Amazon Elasticsearch Service for analytics, organizations can create a robust and cohesive security ecosystem. This level of integration ensures that security controls are consistently applied across the entire data management landscape.
It is also crucial for organizations to establish and regularly review their data governance policies. These policies should define clear guidelines for data classification, access privileges, and incident response procedures. By aligning these policies with industry standards and aws security data lake requirements, organizations can ensure that their AWS data lake remains compliant and secure.
Finally, organizations must be proactive in staying up-to-date with the latest security threats and best practices. The AWS security landscape is constantly evolving, and it is essential to regularly review and update security measures to address emerging vulnerabilities and new attack vectors.
In conclusion, securing an AWS data lake requires a multifaceted approach that combines technical controls, organizational policies, and a security-conscious culture. By implementing best practices for access control, encryption, logging, and integration with other AWS services, organizations can safeguard their valuable data assets and maintain the trust of their customers and stakeholders. As the reliance on aws security data lake-driven decision-making continues to grow, the importance of robust data lake security cannot be overstated.