Data Security Management: Safeguarding Your Information Assets
Organizations face an increasing need to safeguard their priceless information assets in today’s networked and data-driven environment. In order to guarantee the confidentiality, integrity, and accessibility of sensitive data, data security management is essential so in this article, Nettruyen will examine the value of data security management, look at best practices for protecting information assets, and talk about the tactics businesses may use to reduce risks and uphold compliance.
Data Security Management: Safeguarding Your Information Assets Understanding Data

Security Management:
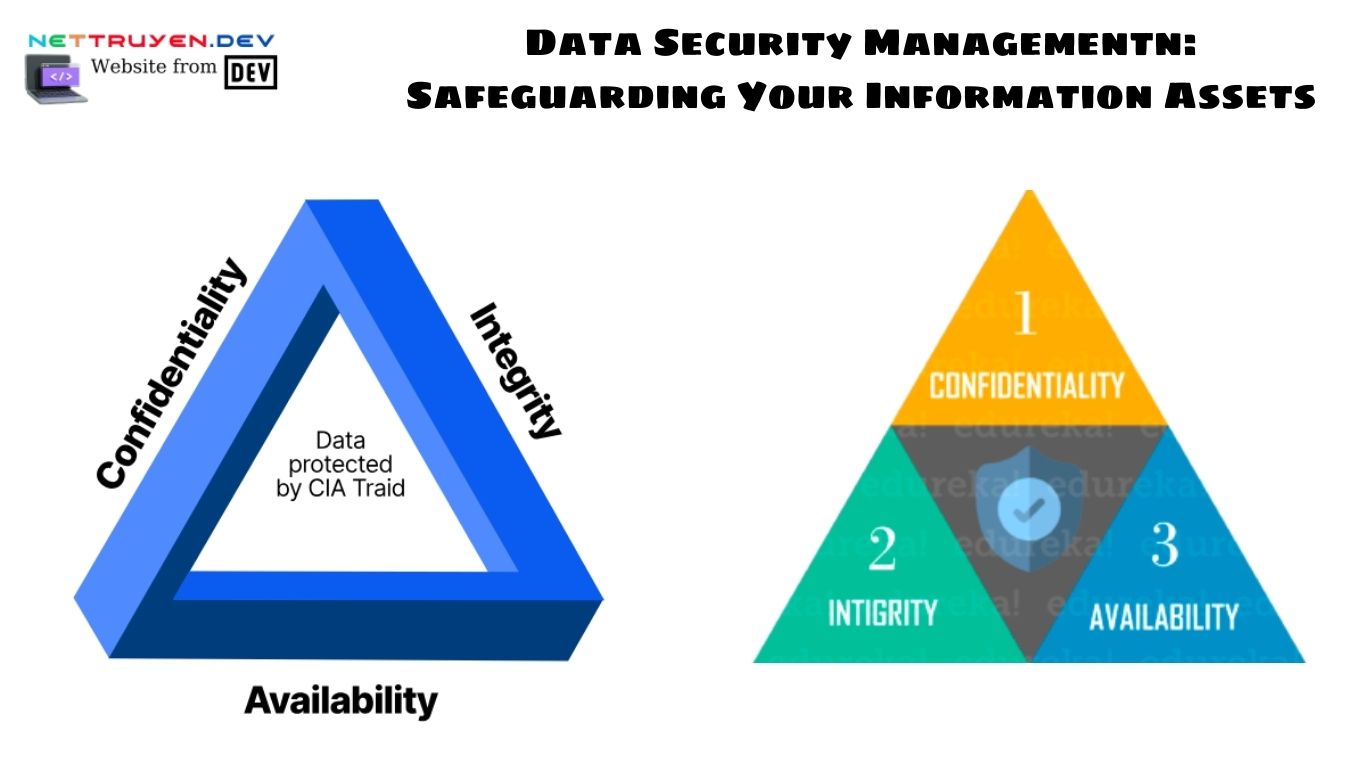
Data security management encompasses the policies, procedures, and technologies implemented to protect data from unauthorized access, use, disclosure, alteration, or destruction. It involves a comprehensive approach that addresses various aspects of information security, including risk assessment, data classification, access controls, encryption, incident response, and employee awareness and training.
The Significance of Data Security Management:
Effective data security management is essential for organizations of all sizes and across industries. It helps safeguard sensitive customer information, intellectual property, financial data, and other critical assets. Failure to adequately protect data can result in reputational damage, financial losses, regulatory penalties, and legal consequences. By prioritizing data security management, organizations demonstrate their commitment to safeguarding the trust and privacy of their stakeholders.
Identifying Information Assets:
Before implementing data security measures, organizations must identify their information assets. This involves conducting a thorough inventory of the data they collect, store, process, and transmit. Information assets can include customer records, employee data, financial information, proprietary research, trade secrets, and any other data that holds value for the organization.
Conducting Risk Assessments:
Risk assessments are crucial in identifying vulnerabilities, evaluating threats, and determining the potential impact of data breaches or security incidents. By conducting regular risk assessments, organizations can proactively identify and prioritize security gaps, enabling them to implement appropriate controls and mitigation strategies.
Implementing Access Controls:
Access controls play a vital role in data security management. Organizations should enforce the principle of least privilege, granting employees access only to the data they need to perform their roles. Strong authentication mechanisms, such as multi-factor authentication, should be implemented to prevent unauthorized access. Regular access reviews and audits also help ensure that access privileges remain up to date and aligned with business requirements.
Encryption for Data Protection:
Encryption is a fundamental component of data security management. By encrypting sensitive data at rest and in transit, organizations add an extra layer of protection. Robust encryption algorithms, secure key management, and the use of digital certificates contribute to the confidentiality and integrity of data, even if it falls into the wrong hands.
Incident Response and Recovery:
Despite best efforts, security incidents may still occur. Implementing an incident response plan is crucial for effectively managing and mitigating the impact of such incidents. Organizations should establish clear procedures for detecting, containing, investigating, and recovering from security breaches. Regularly testing and updating incident response plans is essential to ensure their effectiveness.
Employee
Awareness and Training:
Employees are often the weakest link in data security. Organizations must invest in comprehensive security awareness programs to educate employees about data security risks, best practices, and their responsibilities in protecting information assets. Regular training sessions, phishing simulations, and ongoing communication contribute to establishing a security-conscious culture within the organization.
Compliance with Data Protection Regulations:
Data security management should align with relevant data protection regulations and standards, such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), or industry-specific guidelines. Organizations must understand their compliance obligations, implement necessary controls, and regularly assess their compliance posture.
Continuous Monitoring and Improvement:
Data security management is an ongoing process. Organizations should establish a framework for continuous monitoring, periodic security assessments, and vulnerability management. Regular audits and penetration testing help identify weaknesses and ensure the effectiveness of security controls. By staying updated with emerging threats and industry best practices, organizations can continually improve their data security posture.
Security Audits and Certifications:
Conducting regular security audits and obtaining relevant certifications can provide assurance to stakeholders that an organization has implemented adequate data security measures. Certifications such as ISO 27001 (Information Security Management System) demonstrate a commitment to best practices and can enhance the organization’s reputation.

Conclusion:
Data security management is a crucial aspect of modern business operations. Safeguarding information assets is vital for protecting customer trust, maintaining compliance, and mitigating the risks associated with data breaches. By implementing robust data security measures, including risk assessments, access controls, encryption, incident response, and employee training, organizations can proactively address threats and vulnerabilities. With a comprehensive and proactive approach to data security management, organizations can safeguard their information assets and navigate the evolving landscape of data protection with confidence.
Data security management is an ongoing and dynamic process that requires constant attention and adaptation to emerging threats and regulatory requirements. By implementing a comprehensive and proactive approach, organizations can safeguard their valuable information assets, maintain compliance, and ensure the trust and confidence of their stakeholders.
Conclusion: So above is the Data Security Management: Safeguarding Your Information Assets article. Hopefully with this article you can help you in life, always follow and read our good articles on the website: nettruyen.dev




