Data Security Posture Management: Safeguarding Your Digital Fortress

Introduction to Data Security Posture Management

In an era where data breaches and cyber threats loom large, ensuring the safety of your organization’s sensitive information is paramount. That’s where data security posture management comes into play. But what exactly is it, and why is it crucial to your digital defense?
A. Importance and relevance of data security posture management
Imagine your organization’s data as a fortress, with multiple layers of protection shielding it from malicious intruders. Data security posture management acts as the vigilant guardian, constantly monitoring and fortifying those defenses, ensuring that your data remains secure from any potential breaches.
Think about it: in today’s data-driven world, where companies store vast amounts of valuable information, the consequences of a breach can be devastating. Not only can it compromise your customers’ trust, but it can also lead to financial losses, regulatory penalties, and irreparable damage to your brand’s reputation.
B. Overview of Gartner’s role in evaluating and ranking data security solutions
When it comes to evaluating and ranking data security solutions, Gartner stands tall as a trusted authority. Renowned for its rigorous assessment methodologies, Gartner provides organizations with invaluable insights and guidance in selecting the right data security posture management solution. Their assessments help businesses make informed decisions, ensuring they invest in robust and effective security measures.
Gartner’s evaluations consider a range of factors, including solution capabilities, innovation, customer feedback, and market presence. By analyzing these aspects, Gartner identifies the top vendors in the data security posture management landscape, empowering organizations like yours to make informed choices and fortify their digital fortresses against potential threats.
Stay tuned for the next section, where we delve deeper into the intricacies of data security posture management, equipping you with the knowledge necessary to safeguard your organization’s invaluable data. Remember, in the digital realm, knowledge is power, and securing your data is paramount to keeping your organization safe and thriving.
Understanding Data Security Posture Management

A. Definition and Scope of Data Security Posture Management
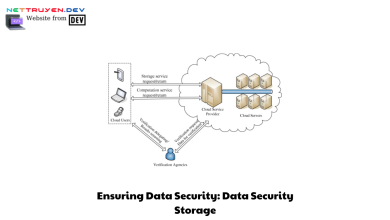
At its core, data security posture management refers to the comprehensive approach an organization takes to continuously assess, manage, and improve its data security measures. It involves evaluating and aligning various security controls, policies, and procedures to ensure the confidentiality, integrity, and availability of data assets.
In simpler terms, data security posture management involves assessing the current state of your organization’s security posture, identifying potential vulnerabilities, and implementing measures to mitigate risks. It goes beyond mere reactive measures and focuses on proactive strategies to safeguard your data against both internal and external threats.
B. Key Components and Functionalities of Data Security Posture Management Solutions
To effectively manage your data security posture, it is essential to understand the key components and functionalities of data security posture management solutions. These solutions provide a centralized platform and tools that enable organizations to monitor, assess, and enhance their security posture continuously.
-
Continuous Monitoring: Data security posture management solutions employ continuous monitoring mechanisms to keep a vigilant eye on your organization’s security environment. This allows for real-time threat detection and response, ensuring that any vulnerabilities or anomalies are promptly addressed.
-
Risk Assessment and Prioritization: These solutions enable organizations to assess the risks associated with their data assets and prioritize their mitigation efforts accordingly. By evaluating vulnerabilities, potential impacts, and likelihoods, businesses can focus their resources on addressing the most critical risks.
-
Compliance and Policy Management: Data security posture management solutions assist organizations in maintaining compliance with industry regulations and internal policies. They offer functionalities for policy creation, enforcement, and monitoring, ensuring adherence to data protection standards.
-
Incident Response and Remediation: Effective incident response and remediation are crucial in minimizing the impact of security incidents. Data security posture management solutions provide tools and workflows to streamline incident response processes, facilitating quick and effective remediation.
Understanding the definition, scope, and key components of data security posture management sets the stage for implementing robust security measures. In the next section, we will explore Gartner’s evaluation criteria for data security posture management solutions, giving you insights into selecting the right solution for your organization’s unique needs.
Gartner’s Evaluation of Data Security Posture Management Solutions
In the ever-evolving landscape of data security, Gartner has established itself as a beacon of expertise, providing comprehensive evaluations of data security posture management solutions. Their rigorous assessments assist organizations in identifying and implementing the most effective measures to protect their valuable data.
A. Gartner’s methodology for evaluating data security posture management solutions
Gartner employs a meticulous methodology to evaluate data security posture management solutions, ensuring a thorough and unbiased assessment process. Their approach combines extensive research, expert analysis, and real-world evaluations. By utilizing this robust methodology, Gartner aims to provide organizations with accurate and reliable insights into the capabilities and effectiveness of various solutions.
B. Criteria used by Gartner to assess the effectiveness and capabilities of solutions
To determine the effectiveness and capabilities of data security posture management solutions, Gartner considers several key criteria. These criteria encompass various aspects, including:
-
Risk Assessment: Gartner evaluates how well solutions assess and analyze potential risks to an organization’s data security posture. This includes identifying vulnerabilities, potential threats, and the ability to prioritize risks based on their impact.
-
Incident Response and Threat Mitigation: Gartner assesses how efficiently solutions detect, respond to, and mitigate security incidents. This includes evaluating the speed and effectiveness of incident response processes, as well as the availability of threat intelligence and automation capabilities.
-
Compliance and Regulatory Support: Gartner examines how well solutions align with industry regulations and data protection standards. This includes evaluating features that facilitate compliance, such as data encryption, access controls, and audit trail capabilities.
C. Gartner’s ranking and classification of top data security posture management vendors
Based on their evaluations, Gartner ranks and classifies the top data security posture management vendors. These rankings help organizations understand the market landscape and identify the most reputable and effective solutions available. By leveraging Gartner’s rankings, organizations can make informed decisions when selecting a data security posture management solution that aligns with their specific needs and requirements.
In the upcoming sections, we will explore the numerous benefits of implementing data security posture management and delve into best practices to fortify your organization’s data defenses. Stay tuned to empower yourself with the knowledge and strategies necessary to protect your digital fortress.
Benefits of Implementing Data Security Posture Management
As organizations increasingly rely on digital infrastructure and data-driven processes, implementing data security posture management brings a multitude of benefits that are vital for safeguarding your valuable information.
A. Enhanced protection against data breaches and cyber threats
Data breaches have become all too common in today’s interconnected world, and the consequences can be severe. By implementing data security posture management, you significantly strengthen your defenses against potential breaches and cyber threats. Through continuous monitoring, proactive risk assessments, and vulnerability management, you can identify and address security gaps before they are exploited by malicious actors. This proactive approach ensures that your data remains confidential, intact, and out of the hands of unauthorized individuals.
B. Improved compliance with industry regulations and data protection standards
In an era of increasing regulatory scrutiny and data protection standards, compliance is more critical than ever. Data security posture management solutions help you stay ahead of the curve by ensuring that your organization meets the necessary industry regulations and data protection standards. By implementing robust security measures, conducting regular audits, and demonstrating a commitment to data privacy, you not only avoid potential penalties but also build trust among your customers and stakeholders.
C. Streamlined incident response and threat mitigation processes
No matter how robust your security measures may be, there is always a possibility of security incidents. In such cases, having a well-defined incident response plan is crucial. Data security posture management solutions provide you with the tools and capabilities to streamline your incident response and threat mitigation processes. With real-time monitoring, automated alerts, and incident management workflows, you can swiftly detect, analyze, and respond to security incidents, minimizing their impact and reducing downtime.
By implementing data security posture management, you not only protect your organization from potential breaches and cyber threats but also ensure compliance with regulations and optimize your incident response capabilities. Stay tuned for the next section, where we explore the best practices for effective data security posture management, helping you establish a robust and comprehensive security strategy. Remember, a proactive approach is the key to maintaining the integrity and security of your data.
Best Practices for Effective Data Security Posture Management
In order to establish a robust data security posture management, it is essential to adopt industry best practices. By following these practices, you can strengthen your organization’s defenses and proactively mitigate potential risks. Let’s explore some key strategies to ensure effective data security posture management.
A. Developing a comprehensive data security strategy
A solid data security strategy serves as the foundation for effective posture management. Start by conducting a thorough assessment of your organization’s data landscape. Identify the types of data you handle, their sensitivity levels, and the potential risks associated with each. This understanding will aid in devising appropriate security measures tailored to your unique requirements.
Next, establish clear policies and procedures to govern data handling, access control, encryption, and incident response. Regularly educate and train employees on these protocols to ensure their compliance and vigilance. Additionally, consider implementing multi-factor authentication and role-based access controls to limit unauthorized access.
B. Implementing continuous monitoring and assessments
Data security is an ongoing process, and continuous monitoring is crucial to identify and respond to threats promptly. Deploy advanced security tools and technologies that provide real-time monitoring capabilities. These solutions can detect anomalies, suspicious activities, and potential vulnerabilities, allowing you to take proactive measures before any damage occurs.
Conduct regular security assessments and penetration tests to identify any weaknesses and potential entry points. This will enable you to address vulnerabilities promptly and ensure your security measures remain effective over time. Additionally, leverage threat intelligence to stay informed about the latest trends and threats in the cybersecurity landscape.
C. Prioritizing risk management and remediation efforts
Risk management should be a top priority when it comes to data security posture management. Conduct regular risk assessments to identify potential vulnerabilities and prioritize them based on their potential impact and likelihood of exploitation. Allocate resources and efforts accordingly to mitigate high-risk areas promptly.
Establish an incident response plan that outlines the steps to be taken in case of a security incident. This plan should include roles and responsibilities, communication protocols, and procedures for containing and resolving the incident. Regularly test and update this plan to ensure its effectiveness.
By implementing these best practices, you can strengthen your organization’s data security posture and effectively mitigate potential risks. Remember, proactive measures and continuous monitoring are key to staying one step ahead in the ever-evolving landscape of data security.
Future Trends and Innovations in Data Security Posture Management
As technology continues to evolve at a rapid pace, so do the tactics and techniques employed by cybercriminals. To stay one step ahead in the battle for data security, organizations must embrace future trends and innovations in data security posture management. Here’s a glimpse into what the future holds:
A. Emerging technologies and their impact on data security posture management
The advent of emerging technologies such as artificial intelligence (AI), machine learning (ML), and blockchain is revolutionizing the data security landscape. AI and ML algorithms can analyze vast amounts of data, identify patterns, and detect anomalies in real-time, enabling organizations to preemptively address potential vulnerabilities. Blockchain, with its decentralized and tamper-proof nature, offers a secure framework for data storage and transactional integrity.
These technologies empower data security posture management solutions with advanced threat detection capabilities, predictive analytics, and automated response mechanisms. By embracing these innovations, organizations can enhance their resilience against ever-evolving cyber threats.
B. Gartner’s predictions for the future of data security posture management
Gartner, with its expertise and foresight, offers valuable predictions for the future of data security posture management. They anticipate an increased focus on risk-based approaches, where organizations prioritize security measures based on the significance of the assets they protect. Context-aware security solutions that adapt to changing environments and user behavior will also gain prominence.
Furthermore, Gartner predicts a shift towards proactive threat hunting and incident response, facilitated by the integration of threat intelligence platforms and security orchestration, automation, and response (SOAR) technologies. These advancements will empower organizations to detect and mitigate threats swiftly, minimizing potential damages.
To stay ahead in managing your data security posture, it is crucial to embrace these emerging trends and innovations. By doing so, you can fortify your digital fortress, ensuring the safety and integrity of your organization’s valuable data.
In conclusion, data security posture management is an essential component of any comprehensive cybersecurity strategy. By understanding its importance, leveraging Gartner’s evaluations, and embracing future trends, you can establish a robust defense against cyber threats. Safeguarding your data is not merely an option; it is a necessity in today’s interconnected digital landscape. So, take the necessary steps to protect your organization’s valuable assets and fortify your data security posture.
Nettruyen.dev is your ally in achieving data security excellence. Stay tuned for more informative articles and insights to help you navigate the ever-changing world of data security. Together, we can build a safer digital future.
Conclusion: So above is the Data Security Posture Management: Safeguarding Your Digital Fortress article. Hopefully with this article you can help you in life, always follow and read our good articles on the website: nettruyen.dev