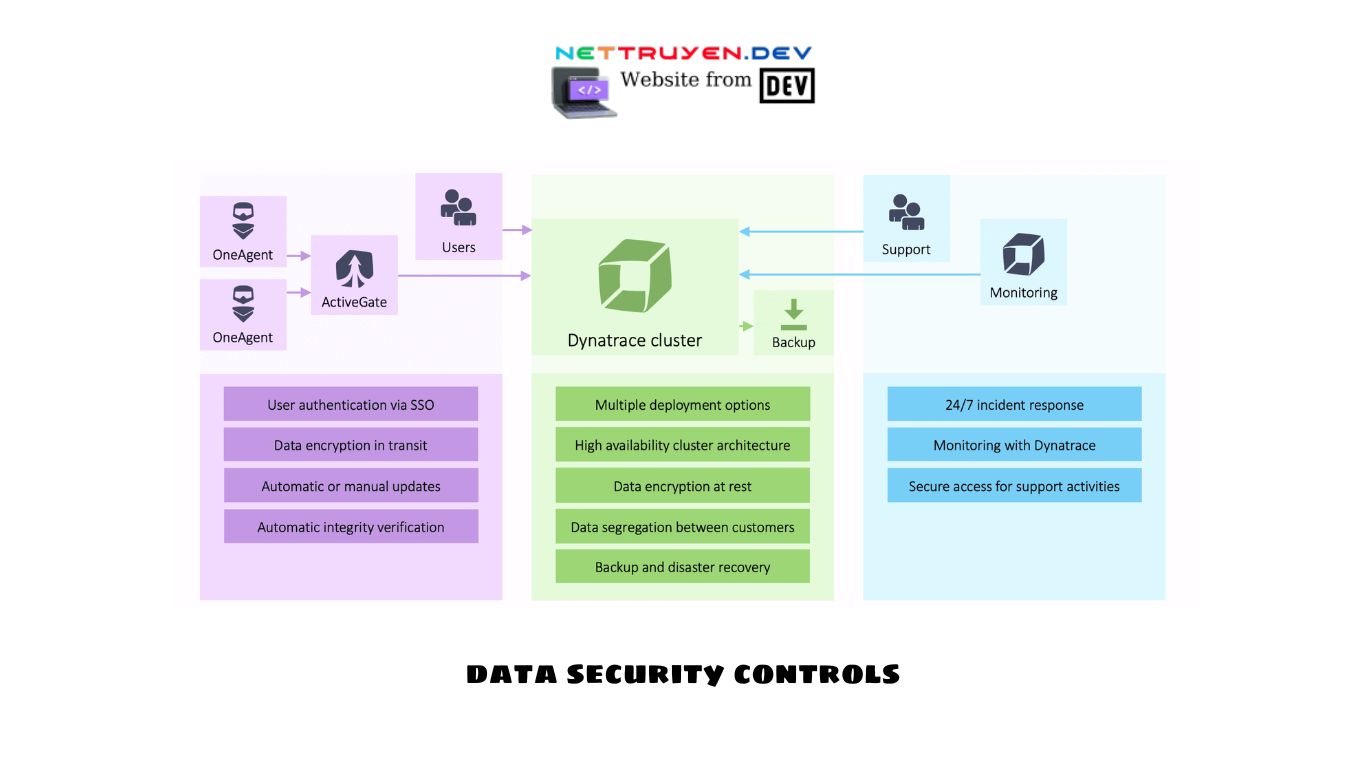
Data Security Controls: Safeguarding Your Valuable Information

In today’s digital age, the protection of valuable information has become paramount. With the increasing reliance on technology and the proliferation of cyber threats, implementing robust data security controls is essential for organizations and individuals alike. In this article, Nettruyen will delve into the world of data security controls, exploring their importance, key components, and best practices for safeguarding your valuable information.
Data Security Controls: Safeguarding Your Valuable Information

- The Significance of Data Security Controls
Begin by highlighting the significance of data security controls in the modern era. Discuss the exponential growth of data and the increasing risks associated with unauthorized access, data breaches, and cyber attacks. Emphasize the potential consequences of data breaches, including financial loss, reputational damage, and legal implications. Explain how data security controls are crucial for mitigating these risks and protecting valuable information.
- Understanding Data Security Controls
Provide a comprehensive explanation of what data security controls entail. Discuss how data security controls are a combination of technical, administrative, and physical safeguards implemented to protect data from unauthorized access, alteration, or destruction. Explain that these controls encompass various measures, including encryption, access controls, auditing, and incident response protocols.
- Key Components of Data Security Controls
Explore the key components that make up effective data security controls. Discuss each component individually, emphasizing their importance in safeguarding valuable information:
- Access Controls: Highlight the significance of controlling who has access to sensitive data and implementing measures such as strong authentication, role-based access control, and least privilege principles.
- Encryption: Explain the role of encryption in protecting data, both at rest and in transit, and discuss different encryption methods, such as symmetric and asymmetric encryption.
- Network Security: Discuss the importance of secure network architectures, firewalls, intrusion detection systems, and network segmentation to prevent unauthorized access and attacks.
- Incident Response: Highlight the need for a well-defined incident response plan to detect, respond to, and recover from security incidents promptly.
- Security Awareness Training: Emphasize the role of educating employees and individuals about data security best practices, such as password hygiene, recognizing phishing attempts, and safe browsing habits.
- Best Practices for Implementing Data Security Controls
Provide a set of best practices for effectively implementing data security controls. Discuss each practice in detail, explaining its significance and potential impact on data protection:
- Conduct Risk Assessments: Explain the importance of regularly assessing risks and vulnerabilities to identify potential security gaps and prioritize control implementation.
- Develop a Data Classification Framework: Discuss the significance of categorizing data based on its sensitivity and implementing appropriate security controls accordingly.
- Implement Strong Authentication: Emphasize the importance of using multi-factor authentication to enhance login security and protect against unauthorized access.
- Regularly Update and Patch Systems: Highlight the need for promptly applying security patches and updates to address known vulnerabilities in software and systems.
- Monitor and Audit: Discuss the significance of monitoring logs and security events to detect anomalies, as well as conducting regular audits to ensure compliance with security policies and controls.
- Emerging Technologies in Data Security Controls
Discuss emerging technologies that are shaping the landscape of data security controls. Highlight advancements such as artificial intelligence (AI) and machine learning (ML) algorithms for threat detection, blockchain for secure transactions, and cloud-based security solutions for enhanced data protection. Explain how these technologies can complement traditional data security controls and provide additional layers of defense.
- Compliance and Regulatory Considerations
Address the compliance and regulatory considerations associated with data security controls. Discuss the importance of adhering to industry-specific regulations, such as the General Data Protection Regulation (GDPR) in the European Union or the Health Insurance Portability and Accountability Act (HIPAA) in the healthcare sector. Highlight the role of data security controls in meeting compliance requirements and avoiding potential legal implications.

- The Human Factor in Data Security Controls
Emphasize the role of individuals in maintaining effective data security controls. Discuss the importance of security awareness training, promoting a culture of security within organizations, and fostering responsible data handling practices among employees. Highlight the need for ongoing education and communication to ensure that individuals understand their role in safeguarding valuable information.
- Data Security Controls in Personal Life
Extend the discussion of data security controls beyond organizational settings to personal life. Discuss the importance of implementing data security controls on personal devices, securing home networks, and being mindful of privacy settings on social media platforms. Provide practical tips for individuals to protect their own valuable information in an increasingly connected world.
- Data Security Controls and the Future
Discuss the evolving nature of data security controls and their future implications. Address emerging trends, such as the Internet of Things (IoT), big data analytics, and the increasing integration of AI in security systems. Highlight the need for continuous adaptation and innovation in data security controls to keep pace with evolving threats.
- Conclusion: Protecting Your Valuable Information
Conclude the article by reinforcing the importance of data security controls in safeguarding valuable information. Summarize the key components and best practices discussed, emphasizing the need for a comprehensive and multi-layered approach to data security. Encouragereaders to prioritize the implementation of data security controls in their organizations and personal lives to protect their valuable information from potential threats. Stress that data security is an ongoing process that requires vigilance, continuous learning, and adaptation to stay one step ahead of cybercriminals. By implementing robust data security controls, individuals and organizations can significantly reduce the risk of data breaches and ensure the safety of their valuable information.
Conclusion: So above is the Data Security Controls: Safeguarding Your Valuable Information article. Hopefully with this article you can help you in life, always follow and read our good articles on the website: nettruyen.dev