Data Security Policies: A Comprehensive Guide
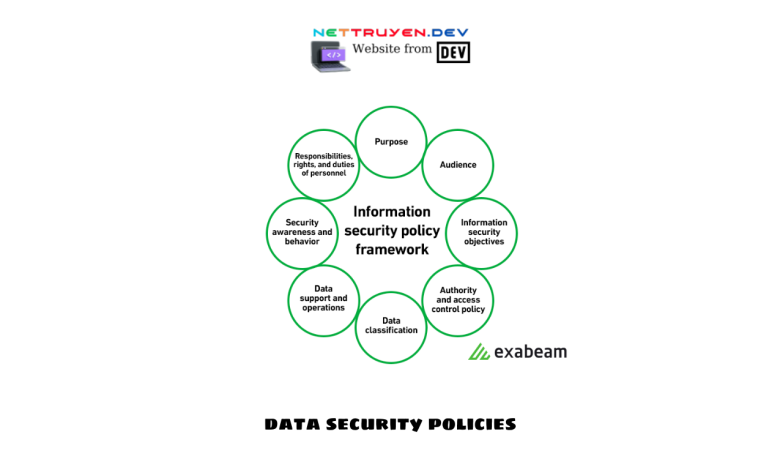
In today’s digital age, Data Security Policies face increasing risks of data breaches and cyber threats. To protect sensitive information and maintain the trust of customers and stakeholders, implementing robust data security policies is crucial. In this comprehensive guide, Nettruyen will delve into the world of data security policies, exploring their importance, key elements, best practices, and the role they play in safeguarding valuable data. By understanding and implementing effective data security policies, organizations can strengthen their defense against cyber threats and ensure the confidentiality, integrity, and availability of their data.
- Understanding Data Security Policies:
Data security policies are a set of guidelines and procedures that outline how an organization protects and manages its data assets. These policies establish rules and best practices for data handling, access controls, encryption, incident response, and overall data protection. By creating a framework for data security, organizations can mitigate risks and maintain compliance with relevant regulations. - Importance of Data Security Policies:
Data security policies are essential for safeguarding sensitive information against unauthorized access, data breaches, and other security threats. They provide a roadmap for employees, contractors, and stakeholders to follow when handling data, ensuring consistent and secure practices throughout the organization. Effective data security policies not only protect valuable assets but also enhance the organization’s reputation and build trust with customers and partners.
- Key Elements of Data Security Policies:
Data security policies should encompass various key elements to ensure comprehensive protection. These elements include data classification, access controls, encryption, incident response, data retention, employee training, and ongoing monitoring. Each element plays a crucial role in establishing a strong foundation for data security within an organization. - Designing Effective Data Security Policies:
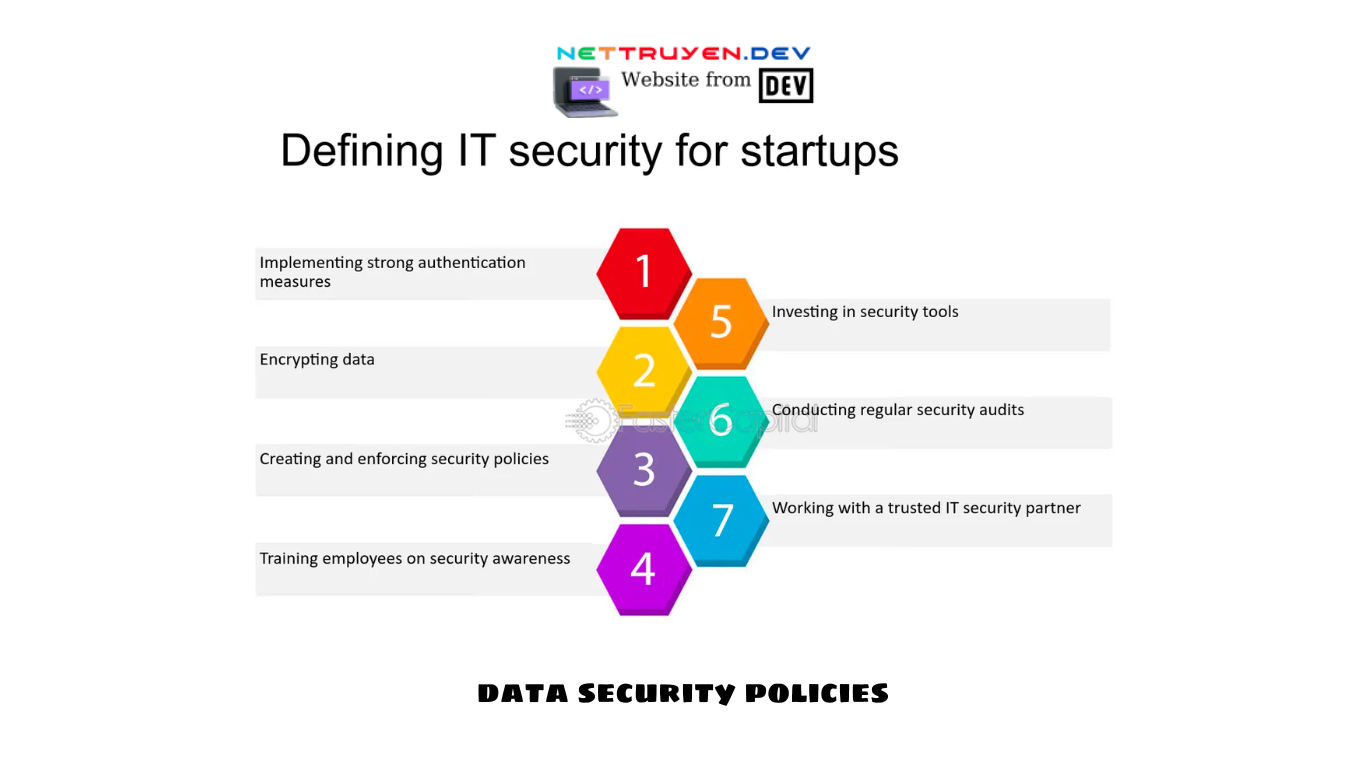
Designing effective data security policies requires a strategic approach. It involves identifying data protection goals, assessing risks and vulnerabilities, defining roles and responsibilities, and establishing clear guidelines for data handling. Policies should be tailored to the organization’s specific needs, taking into account industry regulations, data sensitivity, and the organization’s risk appetite. - Best Practices for Data Security Policies:
To create robust data security policies, organizations should follow industry best practices. These include conducting regular risk assessments, implementing multi-factor authentication, encrypting sensitive data at rest and in transit, establishing strong access controls, regularly patching and updating systems, and conducting employee training on data security awareness. Adopting these best practices can significantly enhance an organization’s data security posture.

- Ensuring Compliance with Data Security Policies:
Data security policies should align with relevant industry regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Compliance with these regulations is essential to avoid legal and financial repercussions. Regular audits and assessments can help ensure that the organization’s data security policies remain compliant and up to date. - Employee Training and Awareness:
Employees play a critical role in maintaining data security. Organizations should provide comprehensive training to employees to raise awareness about data security risks, best practices, and the importance of following data security policies. Training should cover topics such as password hygiene, phishing prevention, social engineering awareness, and incident reporting. By empowering employees with knowledge, organizations can create a culture of data security. - Incident Response and Data Breach Management:
Data security policies should include a well-defined incident response plan to address potential data breaches or security incidents. This plan should outline the steps to be taken in the event of a breach, including containment, investigation, remediation, and notification procedures. By having a robust incident response plan in place, organizations can minimize the impact of security incidents and mitigate potential damages. - Ongoing Monitoring and Evaluation:
Data security policies should be continuously monitored and evaluated to ensure their effectiveness. Regular audits, vulnerability assessments, and penetration testing can help identify areas of improvement and ensure that the policies remain up to date with evolving threats and technologies. Ongoing monitoring also enables organizations to detect and respond to security incidents promptly. - Conclusion:
Data security policies are a critical component of an organization’s overall cybersecurity strategy. By implementing comprehensive and effective data security policies, organizations can protect their valuable data assets, maintain compliance with regulations, and build trust with stakeholders. Through a combination of best practices, employee training, incident response planning, and ongoing monitoring, organizations can establish a robust data security framework that safeguards sensitive information in today’s increasingly complex threat landscape.
Conclusion: So above is the Data Security Policies: A Comprehensive Guide article. Hopefully with this article you can help you in life, always follow and read our good articles on the website: nettruyen.dev



