A Comprehensive Exploration of Secure Data Sharing

In the pulsating heartbeat of the digital age, the exchange of information emerges as the catalyst for innovation, collaboration, and progress. In this interconnected world, where data flows seamlessly between entities, the imperative for sharing is juxtaposed with the critical necessity of safeguarding sensitive information. This comprehensive guide delves deep into the intricacies of “Secure Data Sharing,” unraveling its multifaceted layers, from its profound significance to the complex challenges it presents. As we embark on this journey, we navigate the realms of best practices, cutting-edge technologies, legal considerations, and the evolving landscape that defines the future of secure data sharing.
The Significance of Secure Data Sharing
At the heart of the digital ecosystem, data sharing is the driving force behind collaborative endeavors, research breakthroughs, and transformative technological advancements. It’s the linchpin that connects disparate entities, fostering a collective intelligence that propels industries forward. However, this vast ocean of shared data comes with the inherent responsibility of ensuring its security. As organizations exchange information, the need for robust protocols to protect sensitive data becomes not just a preference but a critical necessity.
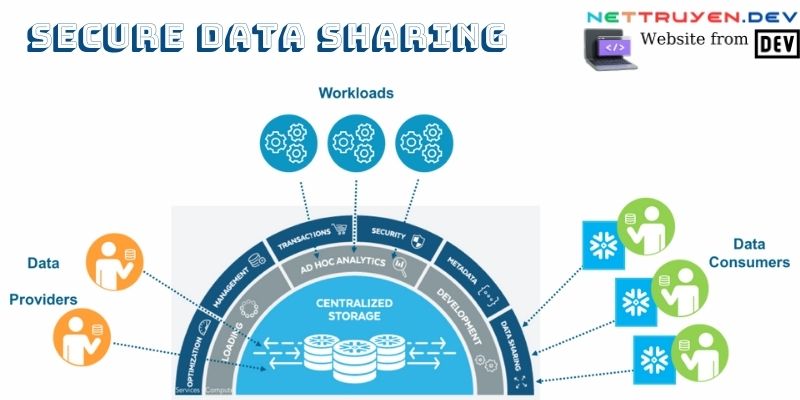
Risks and Challenges in Data Sharing
The digital landscape, while ripe with opportunities, is fraught with risks that demand our unwavering attention. Data breaches, unauthorized access, and integrity issues loom as constant threats that can jeopardize the very foundation of secure data sharing. Moreover, navigating the regulatory landscape adds layers of complexity, with the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and other compliance requirements creating a stringent framework within which data sharing must occur. Understanding these risks and meeting compliance standards become imperative for organizations committed to secure data sharing practices.
Best Practices for Secure Data Sharing
In the pursuit of secure data sharing, organizations must adopt best practices that form the bedrock of their data security infrastructure. Encryption emerges as a formidable shield, ensuring that data remains confidential both in transit and at rest. Robust access controls and stringent authentication measures become the guardians of data, allowing only authorized entities to access and manipulate sensitive information. By weaving these practices into the fabric of their operations, organizations not only protect their data but also fortify their reputations as responsible custodians of information.
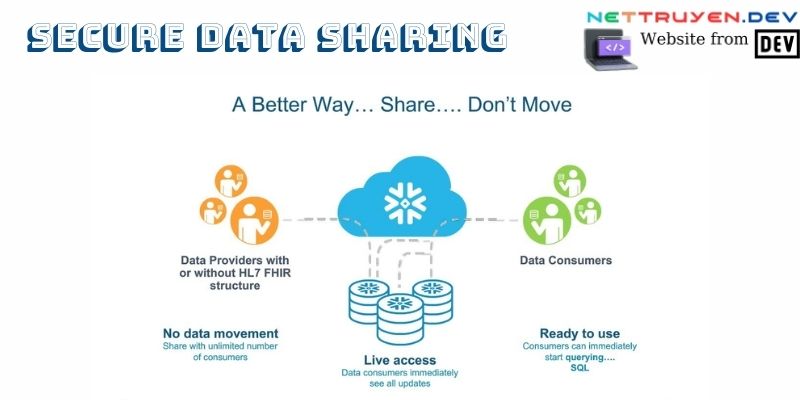
Technologies Enabling Secure Data Sharing
The digital revolution is fueled by innovations that redefine the possibilities of secure data sharing. Among these, blockchain technology stands tall, offering a decentralized and tamper-resistant ledger that enhances the security and transparency of data exchanges. Secure cloud storage solutions further contribute to the seamless and protected exchange of data, leveraging advanced encryption and authentication mechanisms. The integration of these technologies into organizational frameworks ensures that data sharing is not just efficient but also fortified against evolving cyber threats.
Compliance and Legal Considerations
In the ever-evolving landscape of data protection, compliance with legal standards is not just a checkbox; it’s a cornerstone of responsible data sharing. Organizations must navigate the complex web of regulations, ensuring that their data sharing practices align with the legal frameworks that govern their operations. Failure to comply not only poses legal risks but also undermines the trust of stakeholders and exposes organizations to severe consequences. Thus, understanding and adhering to data protection regulations become integral components of the secure data sharing equation.
Data Sharing Protocols and Standards
Established protocols and standards serve as guiding lights in the labyrinth of secure data sharing. These frameworks provide a common language for organizations, ensuring consistency, reliability, and interoperability in their data-sharing practices. Industry-specific standards further elevate the bar, tailoring secure data sharing practices to the unique challenges and requirements of specific sectors. By adhering to these protocols, organizations contribute to a collective effort to standardize and fortify the landscape of secure data sharing.
Case Studies of Secure Data Sharing Implementations
Real-world examples serve as beacons of success, illuminating the path for organizations venturing into the realm of secure data sharing. Case studies provide practical insights into the challenges faced and the strategies employed to overcome them. By examining these real-world scenarios, organizations can glean valuable lessons, understand best practices, and envision the successful implementation of secure data sharing practices within their unique contexts.
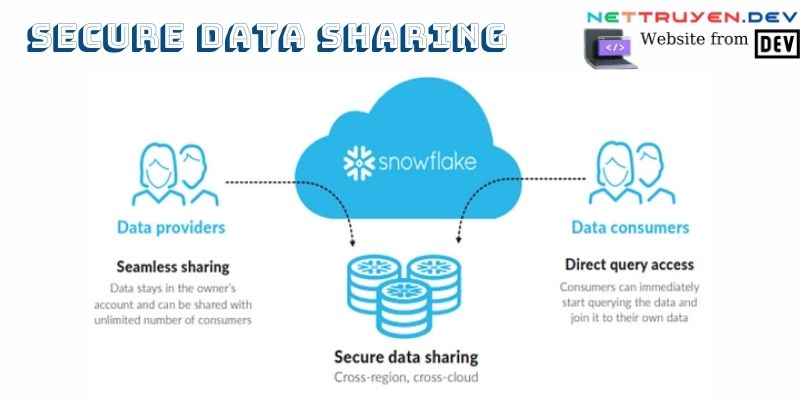
Educating Stakeholders on Secure Data Sharing
In the intricate dance of data sharing, the human element remains a critical factor. Raising awareness and providing comprehensive training to stakeholders within an organization create a culture of vigilance. Cybersecurity policies and guidelines serve as compass points, guiding individuals toward responsible data-sharing practices. By fostering a collective understanding of the risks and best practices, organizations empower their teams to become vigilant guardians of sensitive information.
The Future of Secure Data Sharing
As we stand at the precipice of technological evolution, the future of secure data sharing unfolds with promises of enhanced security, efficiency, and innovation. Emerging technologies like homomorphic encryption are poised to revolutionize data security by enabling computations on encrypted data, ensuring privacy even during data processing. Advancements in decentralized systems, artificial intelligence, and quantum computing further shape the landscape, presenting new possibilities and challenges. The future promises not just the fortification of data security but also the continuous evolution of methodologies and frameworks that define the landscape of secure data sharing.
Conclusion
In conclusion, the exploration of “Secure Data Sharing” is a dynamic odyssey through the intersections of collaboration, innovation, and protection. As we navigate this intricate landscape, the principles of secure data sharing emerge not as obstacles but as guiding stars, illuminating a path toward a future where technological advancements harmonize with robust security protocols. Organizations that prioritize and invest in secure data sharing practices are not only safeguarding their digital assets but are also contributing to a collective effort to shape a safer and more resilient digital future. In this journey, let the principles of secure data sharing be our North Star, guiding us toward a future where innovation and security coexist harmoniously in the digital realm.
Conclusion: So above is the A Comprehensive Exploration of Secure Data Sharing article. Hopefully with this article you can help you in life, always follow and read our good articles on the website: nettruyen.dev



